Starting from Middleware Server Binary Patch 90.10.0 and onwards, there is a change to how IFS Applications sets up the HTTP Server for secured communication. The HTTP Server will no longer be using an HTTP port when HTTPS is configured, it uses the selected main port and configures this for HTTPS communication.
IFS Applications supports secured communication for sensitive information, but not all traffic is routed through HTTPS.
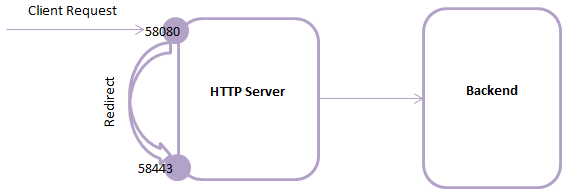
This means that the HTTP Server keeps two ports open, one for
HTTP and one for HTTPS. The main access point to the application always remains the same regardless
of the configuration, and requests are redirected to the HTTPS port when needed. These redirect should not have any noticable effect on performance.

Flow for a request directed to HTTPS (before Middleware Server BP 90.10.0)
The certificate used by Middleware Server (regardless of if importing a third party certificate or creating a self signed certificate) is exported to <ifs_home>/instance/<instance>/conf folder and is named <instance>.cer. If the certificate is not trusted by default, any standalone service that use Java (may it be a Java located in the <ifs_home> or elsewhere) must import this certificate into its trust store or any communication with the server will fail. This has to be done for the correct functionality of the Connect server since it runs as a stand alone java program. Other integrations may also require the certificate to be imported.
If you need to import certificates from third party web services they need to be fetched first. It is possible to use the Internet browser for this purpose by pointing out the third party web service and accepting the certificate in the browser. Most of browsers offer possibility for exporting the downloaded certificates.
But this is also possible to use command line tools for fetching the
certificate: openssl
and sed. Both
those tools are typically preinstalled on Linux but have to be downloaded and
installed on Windows.
The command looks as follows:
Linux:
openssl s_client -connect <hostname>:<port> < /dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
Windows:
openssl s_client -connect <hostname>:<port> < NUL | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <certificate.crt>
A certificate is imported to a truststore by executing the following command:
<java_home>/bin/keytool -import -alias <certificate-alias> -file <certificate.cer> -keystore <truststore> -storepass <thePassword>
-alias: A descriptive name of the imported certificate. Can be chosen freely.
-file: The certificate file to import.
-keystore: The keystore or truststore the certificate shall be imported to. If you plan on using a custom truststore, specify the location and name of that here
(see below for more information) otherwise specify cacerts (<java_home>/jre/lib/security/cacerts)
-storepass: The password for the specified truststore. The default password for cacerts is 'changeit'.
Creating a new truststore can be a convenient way of keeping track of all the certificates used for an installation. It makes it easier to get all certificates imported to a new Java installation and can be easier to maintain when certificates gets old or are no longer needed.
To create a new truststore, execute the following command:
<java_home>/bin/keytool -import -alias <certificate-alias> -file <certificate.cer> -keystore <truststore>
-alias: A descriptive name of the imported certificate. Can be choosen freely.
-file: The certificate file to import.
-keystore: Specify the location for the new truststore. I.e. location and name.
It will prompt for a new password. Carefully choose a secure password for the truststore that has at least six characters.
If merging to cacerts, it's recommended to store the original cacerts together with the custom truststore. This allows you to maintain only the custom truststore and simply overwrite cacerts after merging them.
To merge an existing truststore to cacerts, execute the following command:
<java_home>/bin/keytool.exe -importkeystore -srckeystore <source_truststore> -destkeystore <destination_truststore>
-srckeystore: The trustore to be merged from
-destkeystore: The truststore to be merged to (e.g. <java_home>/jre/lib/security/cacerts).
It will prompt for the password for the source truststore and the password for the destination truststore.