| Foundation1 / Overview / Touch Apps / Touch Apps / |
| Disclaimer: IFS Touch Apps are not bound to a specific version of IFS Applications and the technology and infrastructure might change during the lifespan of IFS Applications 9. The information provided in this section is correct at the time of writing, but for more up to date information please contact your IFS representative. |
At IFS user experience is core to everything we do, with a vision for all users to “Love the application”. This means that we design our apps “phone first” and “touch first”. Each app focuses on a very clear task, presents the important rather than all information, is designed to minimize typing, and looks and feels like an app should. Performance and responsiveness of the user interface is critical to the end user experience, as is the ability of the apps to integrate into the eco system and leverage device features and sensors.
In the world of mobile devices, internet connectivity can rarely be guaranteed. If possible Apps are designed to continue to function without disrupting the user experience even in areas of poor or no connectivity. IFS Touch Apps use SQLite or SQLCipher for on-device storage in order to support offline usage.
IFS Touch Apps communicate with the IFS Touch Apps Cloud or IFS Touch Apps Server using JSON over HTTPS.
IFS Touch Apps are most often single-user apps that rely on device security to protect data. Once a device has been unlocked users can view and act on information in the IFS Touch Apps. There are exceptions to this rule; multi-user apps and apps that handle sensitive data. For these apps a password must be entered every time the app is started, but once the app is up and running it can still be accessed by anyone if the device is left unprotected.
IFS recommend that our customers adhere to best practice routines for protecting their devices. This includes but is not limited to the precautions listed below:
The level of protection required depends on the sensitivity of the data in the particular IFS Touch Apps installed on the device, but a minimum protection level would include a lock screen with pass code, pattern, finger print or equivalent lock method.
Running any app on a rooted/jailbroken device is strongly discouraged for security reasons.
For stronger device protection IFS recommend the use of MDM (Mobile Device Management) software.
IFS Touch Apps are distributed through the standard channels for the different platforms; Apple AppStore, Google Play and Windows Store.
Selected IFS Touch Apps are also made available for download through the IFS Touch Apps Server via the LCS delivery system.
IFS Touch Apps use the same authentication mechanism as
other IFS Applications clients such as IFS Enterprise Explorer. If IFS
Applications has been configured to use LDAP authentication then that is what
IFS Touch Apps will use. If the system has been configured with Oracle
authentication then that is what IFS Touch Apps will use.
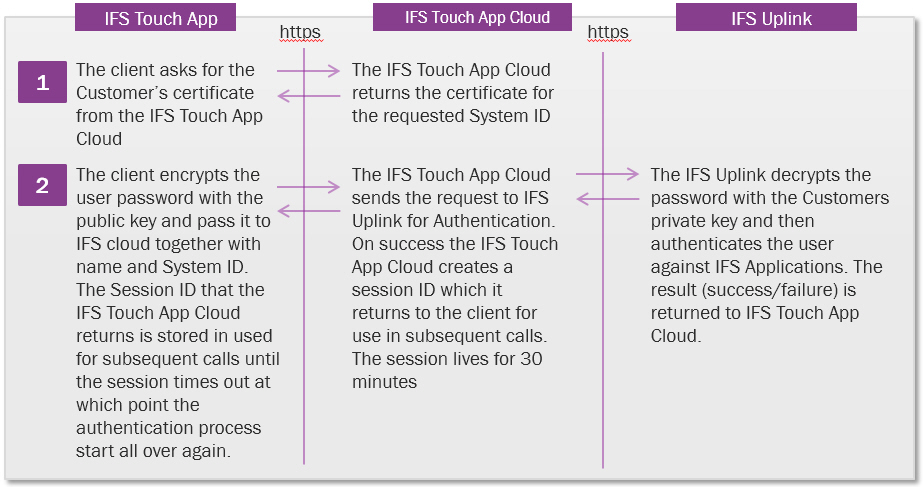
Figure: User Authentication flow chart via IFS Touch Apps Cloud
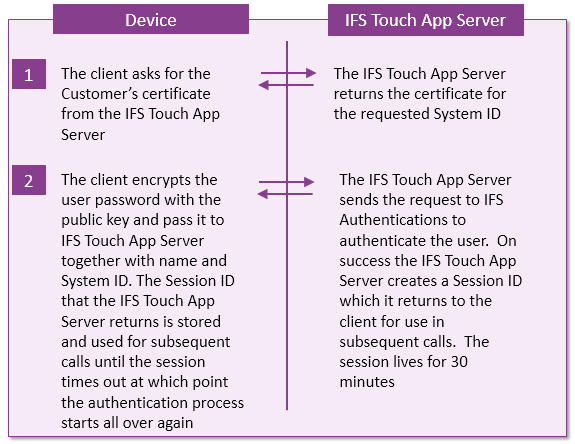
Figure: User Authentication flow chart via IFS Touch Apps Server
Protection of information in the IFS Applications database rests on the same principles as if the IFS Touch Apps were not there. All calls from IFS Touch Apps to IFS Applications are routed through the IFS Uplink or IFS Touch Apps Server which in turn calls IFS Applications using the .NET Access Provider, the same mechanism as used by IFS Enterprise Explorer. This implies that what end users can do from IFS Enterprise Explorer they can also do from an IFS Touch Apps, if enabled for the system, and what they cannot do from IFS Enterprise Explorer they cannot do from an IFS Touch Apps even if the app is enabled for the system.
For IFS Touch Apps dealing with sensitive data it is possible to make use of additional, app specific grants allowing customers to restrict usage of the IFS Touch Apps to selected personnel. This is in addition to the regular privileges required to access the functionality through IFS Enterprise Explorer.