| Foundation1 / Overview / Touch Apps / Uplink / |
| Disclaimer: IFS Touch Apps are not bound to a specific version of IFS Applications and the technology and infrastructure might change during the lifespan of IFS Applications 9. The information provided in this section is correct at the time of writing, but for more up to date information please contact your IFS representative. |
The IFS Uplink acts as an intermediary between the IFS Touch Apps Cloud and the customer’s IFS Applications installations. It can be seen as a high security proxy that on startup connects to and authenticates with the IFS Touch Apps Cloud to establish a trusted connection. The IFS Uplink will then execute commands against IFS Applications on behalf of the IFS Touch Apps Cloud. All commands are run using end user credentials as sent from the mobile device.
The IFS Uplink communicates with IFS Applications using the .Net Access Provider, the same communication library used by IFS Enterprise Explorer.
The IFS Uplink is implemented as a WCF service hosted at the customer site. The service can be monitored using standard Windows monitoring tools. One Windows server can host multiple IFS Uplink services. For best performance the IFS Uplink should be located on the same high speed LAN as the IFS Applications application server.
The IFS Uplink is designed to only accept requests from the IFS Touch Apps Cloud. The key to achieving this is a certificate. The certificate’s private key resides on the machine hosting the IFS Uplink instance. The public key is held in the IFS Touch Apps Cloud and is used to establish a trusted IFS Uplink connection using the authentication procedure detailed here.
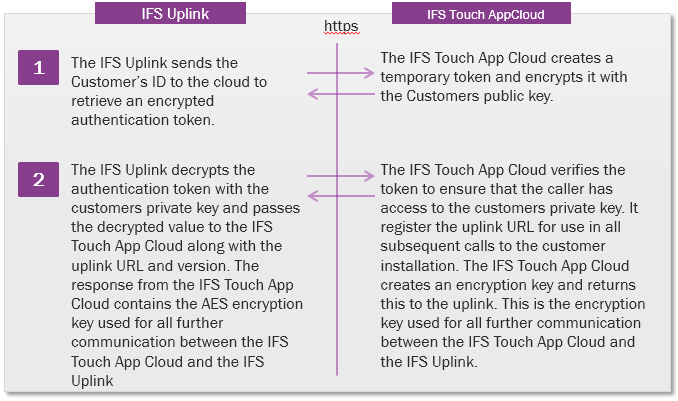
Figure: IFS Uplink authentication flow chart
The encryption key exchanged during the authentication process is used to guarantee the origin of request to the IFS Uplink as coming from the IFS Touch Apps Cloud.
The IFS Uplink should always be protected by a firewall and preferably by a reverse proxy. The firewall must allow access to and from the IFS Touch Apps Cloud but should block all other traffic. Once again best practice standards should be adhered to to protect the service.
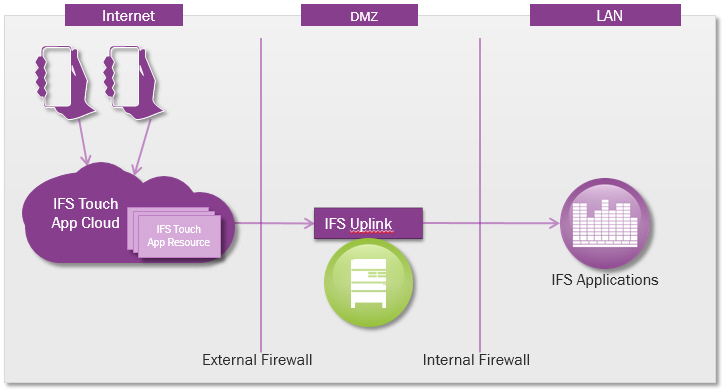
Figure: IFS Uplink installation diagram. Here pictured with the IFS Uplink in a DMZ
The IFS Uplink cannot currently be run in a cluster but supports the use of failover servers to enable high availability installations. Please refer to the IFS Uplink Installation Guide for details.